Remove Blackmail Porn Bitcoin Email Scam
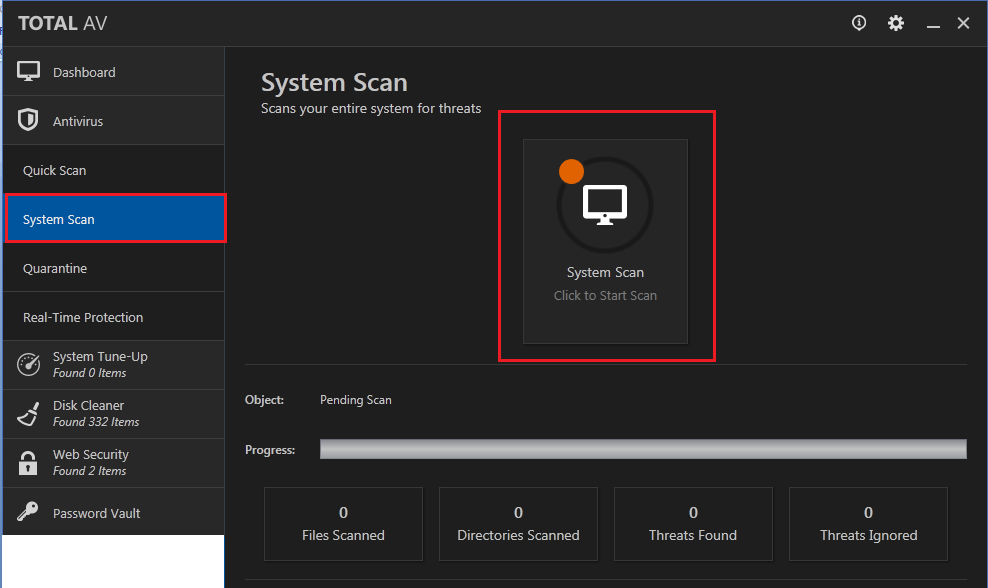
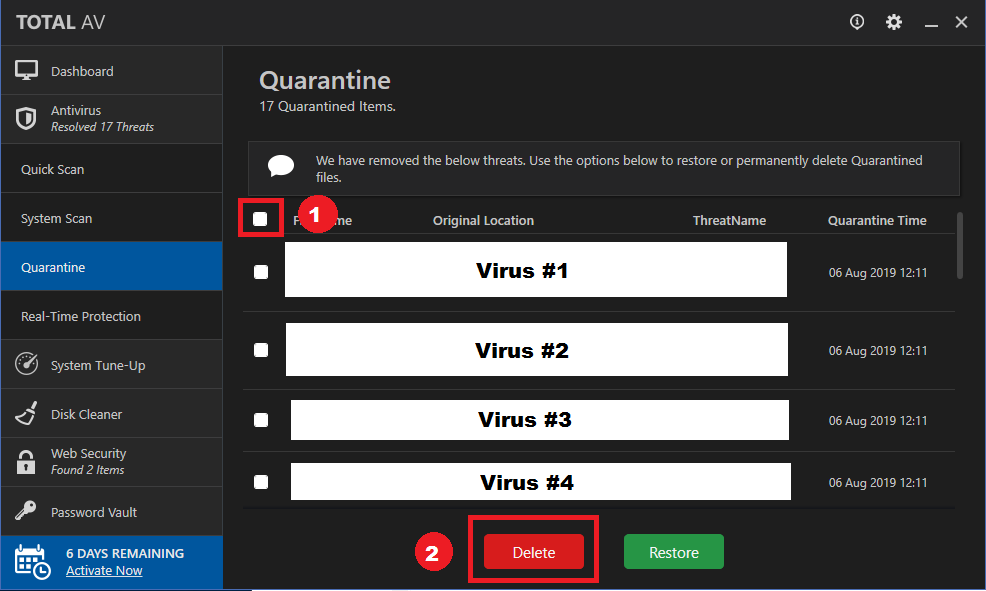
Victims of this scam receive emails that threaten to release compromising images of them if they don’t pay up. Security experts dubbed these intimidating emails as the Blackmail Porn Bitcoin Email Scam. In this article, we will discuss why these threats are only a scam and how you can remove Blackmail Porn Bitcoin Email Scam from your computer.