Viruses are harmful elements that can damage your computer and destroy your precious data. To be sure that you don’t get infected with viruses, try to get download software only from credible sources. You should also avoid ‘free services’ that apparently give off their services for free, but in reality, infect your computer with harmful malware.
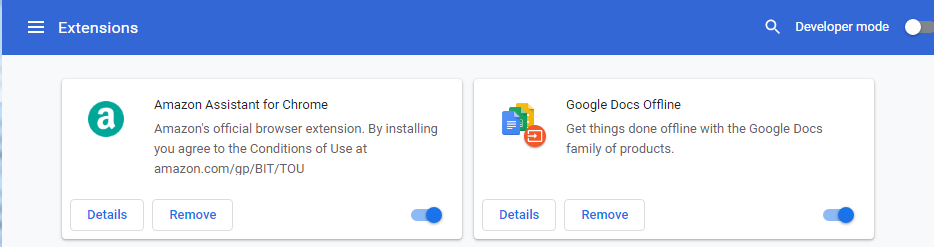
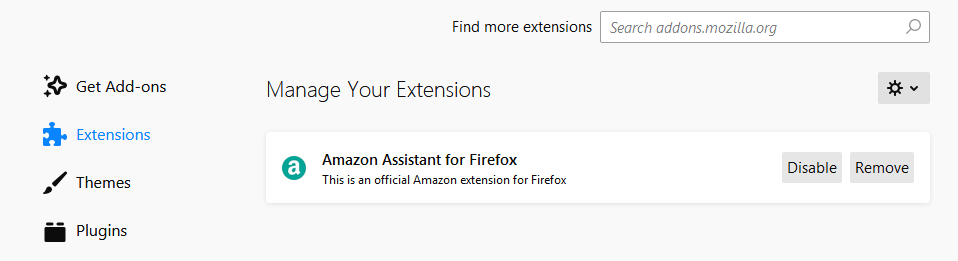
The same can be said about the Amazon Assistant virus. To avoid being a victim of this malware, download the application from Amazon’s original website and make sure that you don’t get infected with viruses.